Following this guide from the Authentik docs, this hint in the Authentik issues list and the Proxmox PVE documentation (1 and 2), I have found a way to map Authentik users, and (admin) groups, to Proxmox PVE.
This works with PVE 8.4.1 at least (but not with PVE 8.3.3), for more than one PVE node with a single Authentik configuration, and even behind NPM (Nginx Proxy Manager).
Authentik configuration
Create Application and Provider
Create an Authentik Application and a Provider according to this guide in the Authentik docs.
However, at least as of today, the guide leaves out one important piece of information: In the Provider configuration, you must set the Encryption Key to blank (—-). Otherwise (meaning if you do set a key here), the authentication will always fail with a 401 error.
Note: In the Provider configuration, you can add as many Redirect URIs/origins as you want, for example if you intend to use Authentik for more than one PVE node. This works with the PVE addresses on port 8006 (e.g. https://nodename.example.tld:8006) as well as with a NPM reverse proxy URL.
Create Authentik group for Proxmox admins
In Authentik go to Directory > Groups and create a group that you want to use for users who shall get admin credentials on your Proxmox PVE nodes (e.g.: “proxmox_admins”). Add users to this group as required.
Proxmox PVE
Add Authentik realm
Add an Authentik realm as described in this guide in the Authentik docs.
To automatically assign admin credentials in Proxmox PVE to users who are member of the group you just created in Authentik (“proxmox_admins”, for example), first set the Proxmox realm’s “Groups Claim” to “groups”:
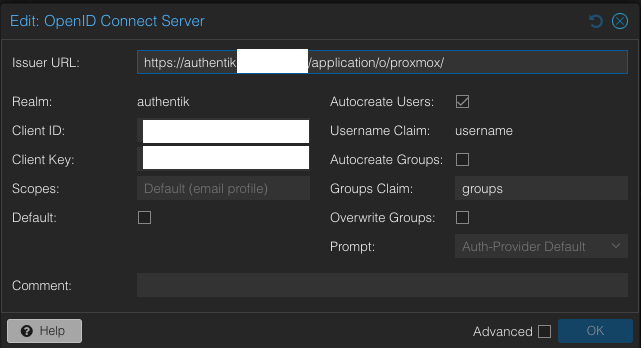
(Note: Authentik itself can sit behind NPM as well.)
Now check if your login to Proxmox PVE via the Authentik realm works (for example by trying to log in in a private browser window).
Create admin group and set ACLs
Now, in Proxmox PVE create a new group named <authentik group name>-<Proxmox PVE realm name>, e.g.: “proxmox_admins-authentik”.
Then open a node shell and type in the following:
pveum acl modify / -group proxmox_admins-authentik -role Administrator(replacing proxmox_admins-authentik with your group name if required) and verify with
pveum acl listwhich should return something like this:
┌──────┬───────────────┬───────┬──────────────────────────┬───────────┐
│ path │ roleid │ type │ ugid │ propagate │
╞══════╪═══════════════╪═══════╪══════════════════════════╪═══════════╡
│ / │ Administrator │ group │ proxmox_admins-authentik │ 1 │
└──────┴───────────────┴───────┴──────────────────────────┴───────────┘
Now if you login via Authentik, Proxmox PVE should assign the Authentik group to the user (to check in Proxmox PVE navigate to Datacenter > Permissions > Users after your first successful authentication; check the “Group” of the user).

Leave a Reply